Pi-hole vs AdGuard Home
Both Pi-hole and AdGuard Home are network-level ad and tracker blocking software. You set your devices to use them as a DNS server, and they filter out domains serving ads or trackers. If you set this as the DNS server for your whole network, it’s a very efficient way to ensure every device makes use of them.
Of course, there’s a lot of argument about the morality of blocking advertisements. Many websites rely on payments from advertisers to remain online (including this one). This is your own decision to make and I’m just reviewing the options available to you.
Licenses
Source code for both pieces of software is available on Github for anyone wanting to look at it. Pi-hole here and Adguard Home here. Pi-hole is released under the EUPL v1.2 and Adguard Home under GPL v3. These are broadly very similar.
Testing Methodology
In order to test these side-by-side, I wanted two identical cloud servers. To this end, I chose a smaller provider, VMHaus. I’m fairly sure they are both on the same physical host, so subject to the same neighbours and are of identical specification – 1GB RAM, 2 AMD EPYC CPU cores and a 15GB SSD disk. I then went ahead and ran some of my standard performance checks to be sure and found the scores to be well matched. I’ve used CentOS 7, fully updated and freshly rebooted to ensure they were clean and ready to go.
Installation
Both Pi-hole and Adguard Home can be installed from source, which is certainly to be recommended if you’re particularly concerned about privacy and security. Equally, both offer single-line install scripts to do the hard work for you.
For Pi-hole this is:
curl -sSL https://install.pi-hole.net | bashAnd for AdGuard Home it’s:
curl -sSL https://raw.githubusercontent.com/AdguardTeam/AdGuardHome/master/scripts/install.sh | shFirst, Pi-hole. The installer first adds the EPEL and Remi repos to gain access to additional software. It’s good that these come from trusted and frequently updated sources to help keep your server secure. The installation completed in 1min 54s. At the end, you’re provided with a link and password to log in.
Now, AdGuard home. The installer just downloads a compressed file, extracts it, and sets it up as a service – the whole time was just 4s! You’re provided with a link to access the interface. You’re then presented with a quick setup where you choose your username/password and determine what interfaces the server will listen on.
First Login
When you first log in to both services, they are relatively similar – offering details of how many DNS queries have been answered, how many blocked, most common domains and details of the clients.
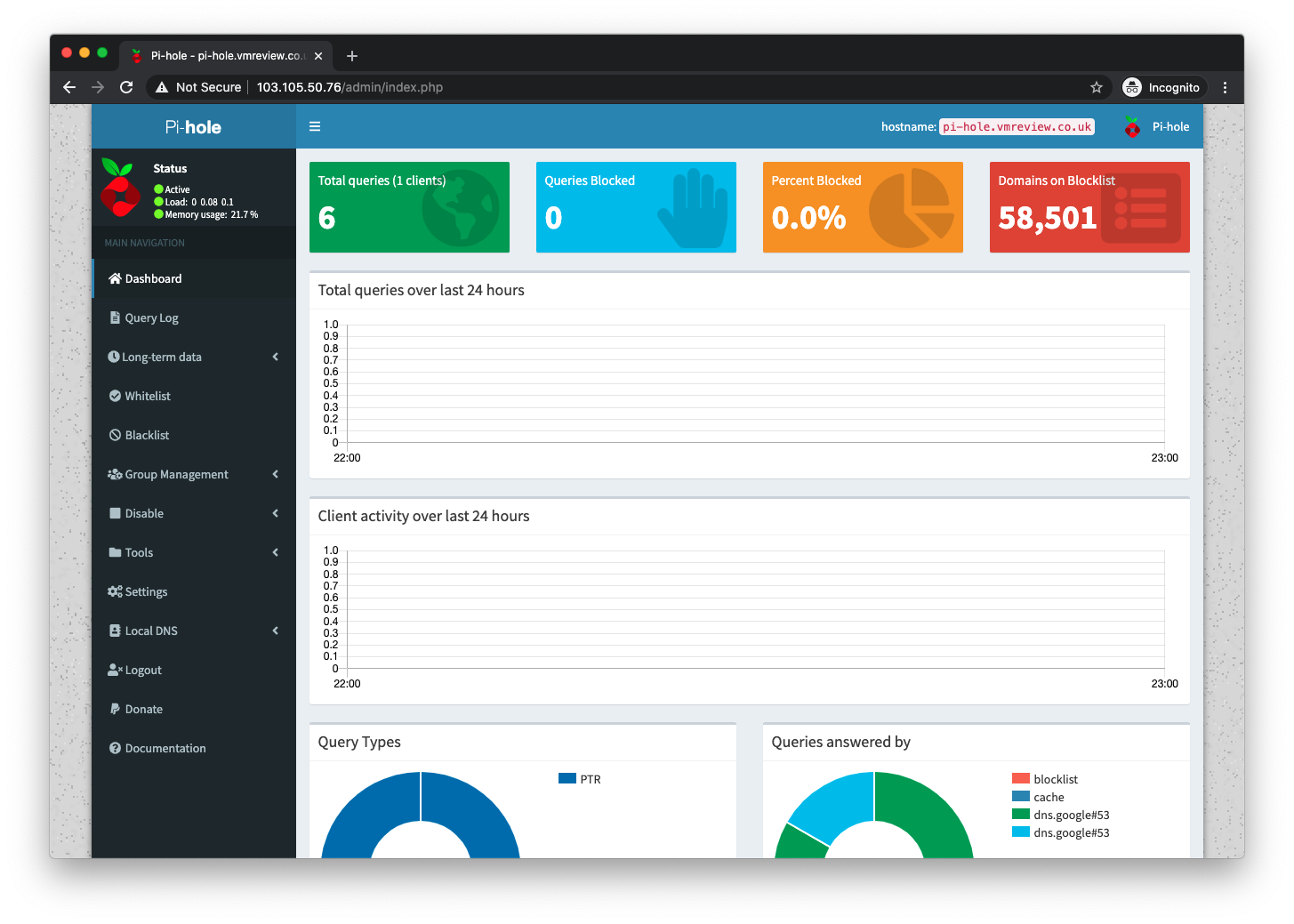
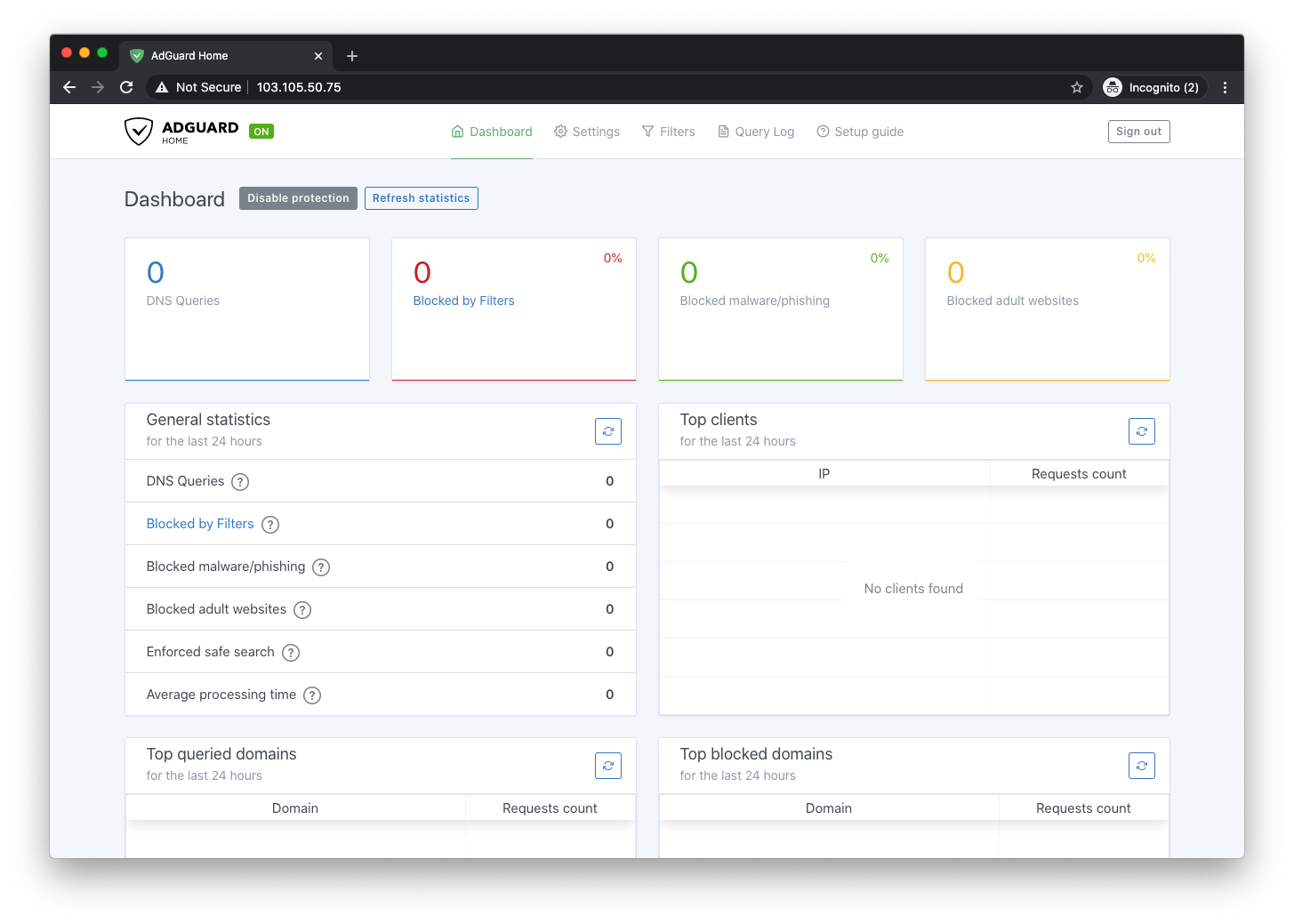
I would say that the AdGuard Home screen looks a little more modern but both are logical and clear.
Resource Usage
Both are very resource-light and would happily run on a small VPS to share with friends and family. AdGuard Home is showing just 130MB of memory used, and Pi-hole just a tiny bit more at 138MB. Disk space is equally light – 1.7GB for AdGuard Home and 1.8GB for Pi-hole – both including a CentOS 7 install. DNS traffic is very light, so even under a heavy load from several users, this wouldn’t stress a small server.
SSL Certificate Installation
Installing a free LetsEncrypt certificate to either piece of software requires a little more command-line work – though neither is particularly difficult. Pi-hole seems the easiest option here, as it’s only used to encrypt the management interface (more on that later). There’s a straightforward guide to achieving it with Caddy here.
For AdGuard Home, the recommended method is to install CertBot and use DNS verification. Again this is fairly easy by following their instructions here. This also enabled some additional features which may be useful to you.
Upstream DNS
For DNS queries that aren’t blocked or cached, both of these utilities will query an upstream DNS server to get the answer for you. Pi-hole defaults to Google’s DNS servers, whilst AdGuard Home defaults to Quad9. Interestingly, the AdGuard Home default is over https rather than conventional DNS, which is more secure.
Both can be configured to use any DNS resolver you wish – though AdGuard Home also offers the ability to use DNS-over-TLS and DNS-over-HTTPS for the upstream.


Blocklists/Allowlists
By default, Pi-hole blocks 58,866 domains from a single public database. AdGuard Home blocks 39.928 from their own (but also public) database. Both have the option to add another list from malwaredomains.com but this appears to be defunct. In both cases you can add any other listings of your choice – AdGuard has a tick box to add the ‘AdAway’ list, for instance. It would seem likely that the almost 20,000 extra domains in the Pi-hole list will improve it’s blocking performance out of the box.
Inevitably with DNS blocking, some false positives will occur – but both offer an easy way to add individual domains to the allowlist that you wish to access. AdGuard Home also has an option to use a public or private allowlist.
Features
| Feature | Pi-hole | AdGuard Home |
| Ad Blocking |  |
 |
| Malware Blocking |  |
 |
| DHCP Server |  |
 |
| IPv4 & IPv6 |  |
 |
| Custom Blocklists |  |
 |
| Custom UpSteam |  |
 |
| DNS-over-HTTPS |  |
 |
| DNS-over-TLS |  |
 |
| DNSSEC |  |
 |
| DNS re-writes |  |
 |
| Built in https support |  |
 |
| Block Services |  |
 |
| Show top domains |  |
 |
Performance
In order to test the speed of the resolver, I used a small script created by CleanBrowsing and shared on GitHub. I also set both to use Quad9 as their upstream to make the test fair.
After freshly rebooting, the Pi-hole was marginally faster – showing an average query time of 4.30ms, compared the AdGuard Home at 6.80ms. Interestingly, a direct query to Google’s 8.8.8.8 showed an average of 7.00ms – slightly slower. Once all the results were cached (as they would be for any domain you use frequently) the times dropped to 2.00 for AdGuard Home and 1.40ms for Pi-hole.
Summary
Either of these pieces of software provide an excellent way to block trackers and adverts. This will speed up your access to many websites and help you stay more private online.
AdGuard Home’s biggest advantage is its implementation of DNS-over-HTTPS and DNS-over-TLS, both for connecting to it and how it connects to your upstream providers. I’m aware this can be added to Pi-hole but it’s far from easy.
Pi-hole’s biggest advantage, in my opinion, is it’s wider usage and hence more audited codebase. It has also performed slightly faster in my tests.
I doubt anyone would be disappointed with either piece of software but for me, AdGuard Home’s encryption features just clinch it.
Recent Posts
Recent Comments
- anonymous1024 on Pi-hole vs AdGuard Home
- Konrad on Add https to Pi-hole with caddy
- jolu on Add LetsEncrypt SSL certificate to Pi-hole
- Mike on Add https to Pi-hole with caddy
- Kamyar on Pi-hole vs AdGuard Home

5 Comments. Leave new
Nice review. I use pihole, openvpn, and unbound on an odroid nic connected and happy with results.
For pi hole there is an android app that displays your traffic. So you are able to watch TV and if something doesn’t work you are able to add or delete domains. Something I was not able to find for AdGuard.
first you need to setup a static dns for your adguard home host pc, say 192.168.6.66
then make sure adguard home interface ip is that one or “all”
then you can access that domain from pretty much all devices connected to the same network can access the interface.
you can even get a domain for it by adding a custom domain for ip in adguard home, like “4872adgh.com”. make sure you dont use some domain that already exists. to be sure, ping that domain before you assign it to adguard home
First of all, thank you for the nice review.
Secondly, Earlier I was unable to come to a conclusion between these two AdGuard or Pi-hole. After reading this article, I decided to stick with Pi-hole. Since it is free, user-friendly, performance, and more graphical. Easy to customize and regular updates.
Yes if you need DNS-over-TLS and DNS-over-HTTPS for the upstream use AdGuard or else Pi-hole is better.
adguard-home just randomly died on me a few days ago after a few weeks of use. Nothing I could do to bring it back to life. Tried docker way of installing, installing from binary, compiling the source, installing from snap, tried every different configuration of network interfaces, not a sausage. Many hours to no avail. Connection to port 53 was properly made, but kept getting SERVFAIL when I tried to test it with nslookup. It’s not reliable. After I switched to pihole, within 10 minutes of cloning the docker-pi-hole github repo, I was up and running and blocking ads again! Yes, DNS-over-HTTPS is an extremely important security feature, but apparently (https://docs.pi-hole.net/guides/dns/cloudflared/) it is very easy to add to pihole. Never going back to adguard.